Bounded Customization in action: Codasip L150 and CORDIC acceleration for motor control
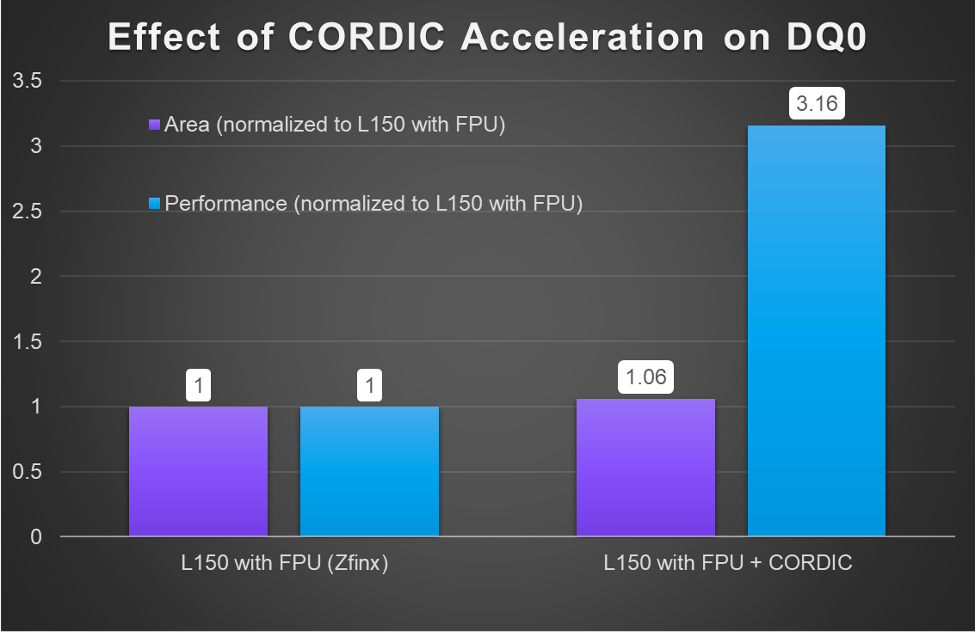
Electric motors are at the core of many automotive innovations; from high-efficiency powertrain and steer-by-wire systems to regenerative braking and active suspension. Whilst standard RISC-V embedded cores provide general baseline capabilities, performance, power, and cost can be optimized by adding dedicated custom instructions. In this blog, we introduce the new Codasip L150: a 3-stage, 32-bit […]
Unlock early software development for custom RISC-V designs with faster simulation

When designing complex Systems-on-Chip, software teams should be involved early in the process. This will help identify architectural bottlenecks, validate system behavior, and accelerate the entire project timeline. In this process, processor simulation models play a crucial role. Processor models work as digital representations of a core and are useful from the initial stages of […]
Design and implementation of a hardened cryptographic coprocessor for a RISC-V 128-bit core
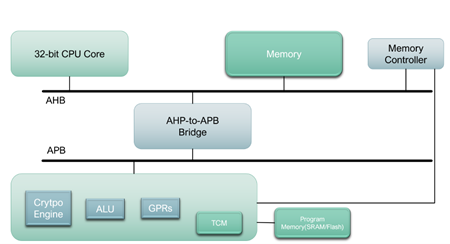

Cryptography is a way of encoding and decoding information to guarantee its confidentiality and protection from unauthorised individuals. Within the realm of digital security and cryptographic algorithms, digital signatures play a critical role in establishing trust. Analogous to a physical signature, digital signatures leverage cryptographic algorithms to generate a unique mathematical fingerprint linked to the […]
Defining the software/hardware interface: A new paradigm enabled by Codasip Studio Fusion



by Keith Graham Before there was a mainstream open standard Instruction Set Architecture (ISA) like RISC-V, a computer processor’s software/hardware interface was generally defined by processor architects. The decisions of the instructions set, multi-issue, out-of-order, speculation, branch prediction or multi-core were to accelerate general purpose or a class, such as Digital Signal Processing (DSP), of […]
Effectively hiding sensitive data with RISC-V Zk and custom instructions
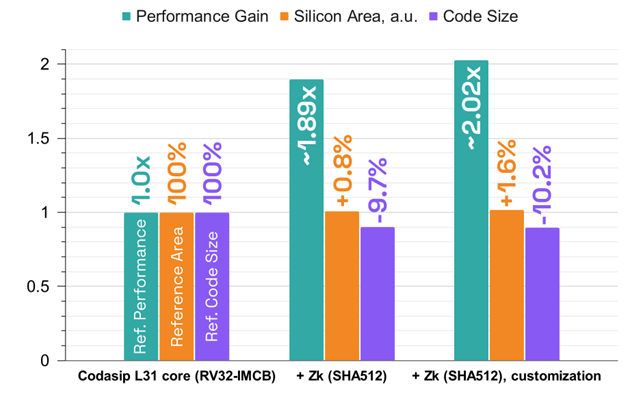

Cryptographic hash functions play a critical role in computer security providing a one-way transformation of sensitive data. Many information-security applications benefit from using hash functions, specifically digital signatures, message authentication codes, and other forms of authentication. The calculation of hash functions such as SHA512, SHA256, MD5 etc is a potential playground for Custom Compute. This […]