by Ron Black
Codasip announced a commercially available RISC-V processor with CHERI for license in October of 2023 and is demonstrating technology for IP provenance.
Dear Members of the Science, Innovation and Technology Committee,
Let me start by applauding your hearing on 24 April 2024, and in particular the evidence of Professor John Goodacre, Challenge Director of Digital Security by Design at Innovate UK, and Mr Richard Grisenthwaite, Executive Vice President and Chief Architect at Arm. During this hearing, the witnesses discussed two extremely important cybersecurity issues: memory safety and IP provenance. In this letter, I would like to provide additional information about these topics that the committee should find relevant.
Memory Safety and CHERI
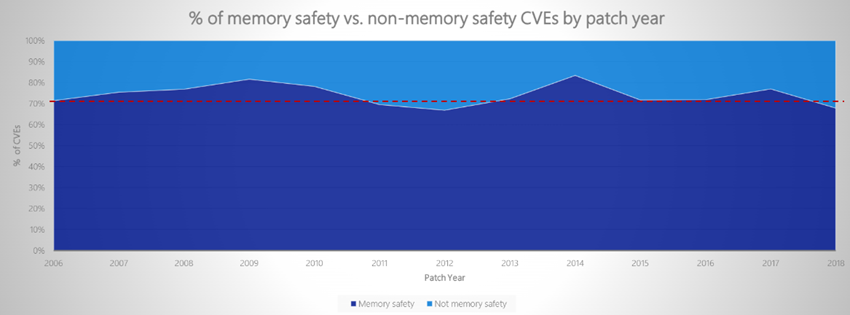
As discussed in the hearing, memory safety issues represent roughly 70-80% of the cyber issues being tracked by the industry. These issues are referred to as Common Vulnerabilities and Exposures, or CVEs. The number of CVEs has grown exponentially over the last twenty years while the percentage of memory safety CVEs has been roughly constant.
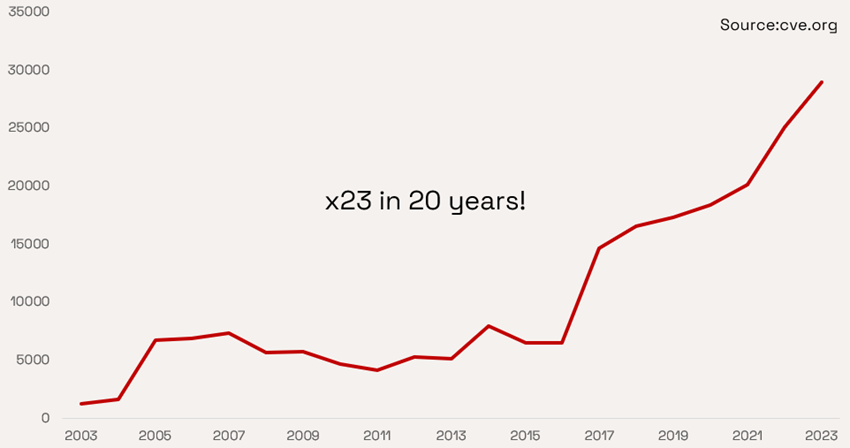
The reason is primarily related to the fact that most software is written in languages like C and C++, which do not provide inherent memory protection. What complicates the problem even more is that software is not normally developed monolithically, but by integrating pre-developed software from third parties, including open-source, where absolutely anyone can contribute potentially malicious changes.
A rough estimate is that over one trillion lines of code are in use today, an enormous amount! The software industry has improved over the last decades, especially regarding “verification”, which is the part of the development process that checks for bugs and corrects them. However, as verification will never be perfect, nor will any developer, there will always be bugs for hackers to exploit in cyberattacks.
The UK is not alone in noticing the enormous memory security issue as the United States White House did a press release on 26 February 2024 entitled: Future Software Should Be Memory Safe.
As Professor Goodacre and Mr Grisenthwaite noted in the hearing, there are economic challenges for companies to take action to address memory safety issues, so they have been slow to do so, even where solutions are readily available. You may think of this situation as similar to the automotive industry’s challenge in adopting safety features that are standard today: seat belts, airbags, and crumple zones. It took decades to have such basic features in all automobiles, and it was only after regulations required them that every manufacturer did so.
For cyberattacks, whilst they are increasingly devastating, causing roughly $10 trillion of economic loss worldwide each year, the direct impact on each company is small enough that all too many do not choose to protect their customers.
In the US, the White House has realised this fact and indicates in its press release that it will be taking action “…shifting the responsibility of cybersecurity away from individuals and small businesses and onto large organizations like technology companies and the Federal Government that are more capable of managing the ever-evolving threat.”
Over the last decade, Professor Goodacre has led outstanding work on CHERI at Digital Security by Design (DSbD), partnering with universities such as the University of Cambridge and semiconductor companies such as Arm. Indeed, Arm has produced a valuable CHERI research platform called Morello. During the hearing, Professor Goodacre noted that despite this exceptional work, the problem in general and specifically with Morello is that it is not a commercial offering, and consequently the industry has not been able to deploy CHERI. Whilst this has been true, I am pleased to update the committee that Codasip has recently launched a commercially available CHERI processor for license and has committed to making its entire portfolio of processors available with CHERI variants. We are also working very closely with the University of Cambridge and other companies to ensure CHERI is standardised and available to everyone.
Design Provenance and Traceability
The second topic discussed by Professor Goodacre and Mr Grisenthwaite was design provenance, which we believe must also include traceability. By provenance, we mean the origin of the design, including knowing the specific designers. By traceability, we mean changes to the design over time, including knowing the specific designers that made the changes. Additional information regarding the design, such as when, where, and with what tools changes were made should also be collected.
As Professor Goodacre and Mr Grisenthwaite explained, most semiconductor chips today are complete systems in themselves containing billions of transistors. Given the incredible complexity, chips are not designed monolithically, transistor by transistor, but assembled from pre-designed “IP blocks”, such as processors, memory, on-chip interconnects between IP blocks, and chip-to-chip interconnects such as USB. Companies like Arm and Codasip make processor IP blocks, while companies like Synopsys and Cadence make memory and chip-to-chip interconnects. Indeed, there is an entire IP industry for semiconductors. As Professor Goodacre and Mr Grisenthwaite discussed during the hearing, some IP are more prone to cyber issues than others, with processors being the most important and problematic.
For the previously discussed topic of memory security, CHERI involves invasive changes to the processor and lesser changes to memory. The additional cybersecurity challenge regarding provenance and traceability is that when one licenses IP blocks, one does not know who actually designed the IP, nor its possible history of modification. Consequently, when the inevitable bugs are found, it is not possible to irrefutably determine who made the errors. Most bugs will be accidental, but it is also possible that nefarious actors could have inserted malicious circuitry to appear as an accidental bug. We believe that provenance and traceability will increase in importance as cyberattacks increase in frequency and are increasingly used in military conflicts – indeed the Economist recently noted “The cyberwar in Ukraine is as crucial as the battle in the trenches”.
Fortunately, Codasip is also addressing the problem of provenance and traceability with a new software tool using blockchain technology to irrefutably log the processor design process and create a record of provenance with traceability. This new software tool is currently being demonstrated to customers in a pre-release version.
So, in summary, Codasip today has solutions to the two major problems that the committee identified in their hearing: (i) commercial availability of CHERI-based processors; and (ii) methods for providence and traceability of semiconductor IP blocks. Much of this work was and is being done in the UK, and the rest is done solely in Europe as we do not have R&D in other geographies.
If the committee has further interest in the technology we are making available, it would be a pleasure to arrange a meeting at your convenience.
Sincerely yours,

Dr Ron Black
CEO, Codasip GmbH
About Dr. Ron Black
Dr Black, CEO at Codasip since 2021, has over 30 years of industry experience. Before joining Codasip, he was President and CEO at Imagination Technologies and previously CEO at Rambus, MobiWire, UPEK, and Wavecom. He holds a BS and MS in Engineering and a Ph.D. in Materials science from Cornell University. A consistent thread of his career has been processors including PowerPC at IBM, network processors at Freescale, security processors at Rambus, and GPUs and CPUs at Imagination.
About Codasip
Codasip is a processor technology company enabling system-on-chip developers to differentiate their products for competitive advantage. Codasip is based in Munich and has development centres throughout Europe, including in Bristol and Cambridge in the UK. The company specializes in processors based on RISC-V (Reduced Instruction Set Computing, Generation Five), which is an open Instruction Set Architecture (ISA) alternative to proprietary architectures such as Arm and Intel x86. Codasip also has extensive experience in cybersecurity, with a team in Bristol that has spent the last two years architecting and designing the recently announced CHERI processor.
